
Securing Your Next.js Startup: A Comprehensive Cybersecurity Guide
In today's digital landscape, startups built on Next.js are thriving. Its speed, scalability, and developer-friendly features make it a top choice for modern web applications. But with great power comes great responsibility – especially regarding cybersecurity. A single breach can cripple a fledgling company, erode customer trust, and derail growth.
At Cyber AR, we specialize in protecting innovative startups like yours. This guide provides actionable steps to secure your Next.js application from day one, ensuring your brilliant idea doesn’t become a hacker’s target.
Why Next.js Security is Non-Negotiable for Startups
Next.js offers powerful features like server-side rendering (SSR), static site generation (SSG), and API routes – but each introduces unique vulnerabilities. Startups are prime targets for attackers because:
- Limited Resources: Security often takes a backseat to speed-to-market.
- Sensitive Data: User data, payment info, and intellectual property are high-value targets.
- Reputation Impact: A breach can destroy trust before you’ve even scaled.
Ignoring security isn’t an option. Let’s fix that.
5 Critical Next.js Security Threats (and How to Stop Them)
1. Injection Attacks (XSS & SQLi)
- Risk: Malicious code injected into your app via forms, URLs, or APIs.
- Next.js Fix:
- Use
next/scriptwithstrategy="afterInteractive"for third-party scripts. - Sanitize user input with libraries like
DOMPurify. - Parameterize database queries (use ORMs like Prisma or Sequelize).
- Use
2. Insecure API Routes
- Risk: Exposed endpoints leaking data or allowing unauthorized actions.
- Next.js Fix:
- Implement authentication (e.g., NextAuth.js, Auth0) for all API routes.
- Validate requests with
zodorjoi. - Rate-limit APIs using middleware (
next-rate-limiter).
3. Server-Side Vulnerabilities
- Risk: SSR/SSG exposing environment variables or server logic.
- Next.js Fix:
- Never expose secrets in client-side code. Use
NEXT_PUBLIC_*sparingly. - Store secrets in
.env.local(excluded from Git). - Use
getServerSideProps/getStaticPropssecurely – avoid passing sensitive data to the client.
- Never expose secrets in client-side code. Use
4. Cross-Site Request Forgery (CSRF)
- Risk: Attackers tricking users into actions without consent.
- Next.js Fix:
- Use
SameSitecookies (__Secure-prefix). - Implement CSRF tokens for state-changing requests (e.g.,
csurfmiddleware).
- Use
5. Dependency Vulnerabilities
- Risk: Outdated packages with known exploits.
- Next.js Fix:
- Run
npm audit fixoryarn auditweekly. - Use
SnykorGitHub Dependabotfor automated scanning.
- Run
Beyond Basics: Proactive Security for Scaling Startups
Once you’ve covered the fundamentals, level up with these advanced measures:
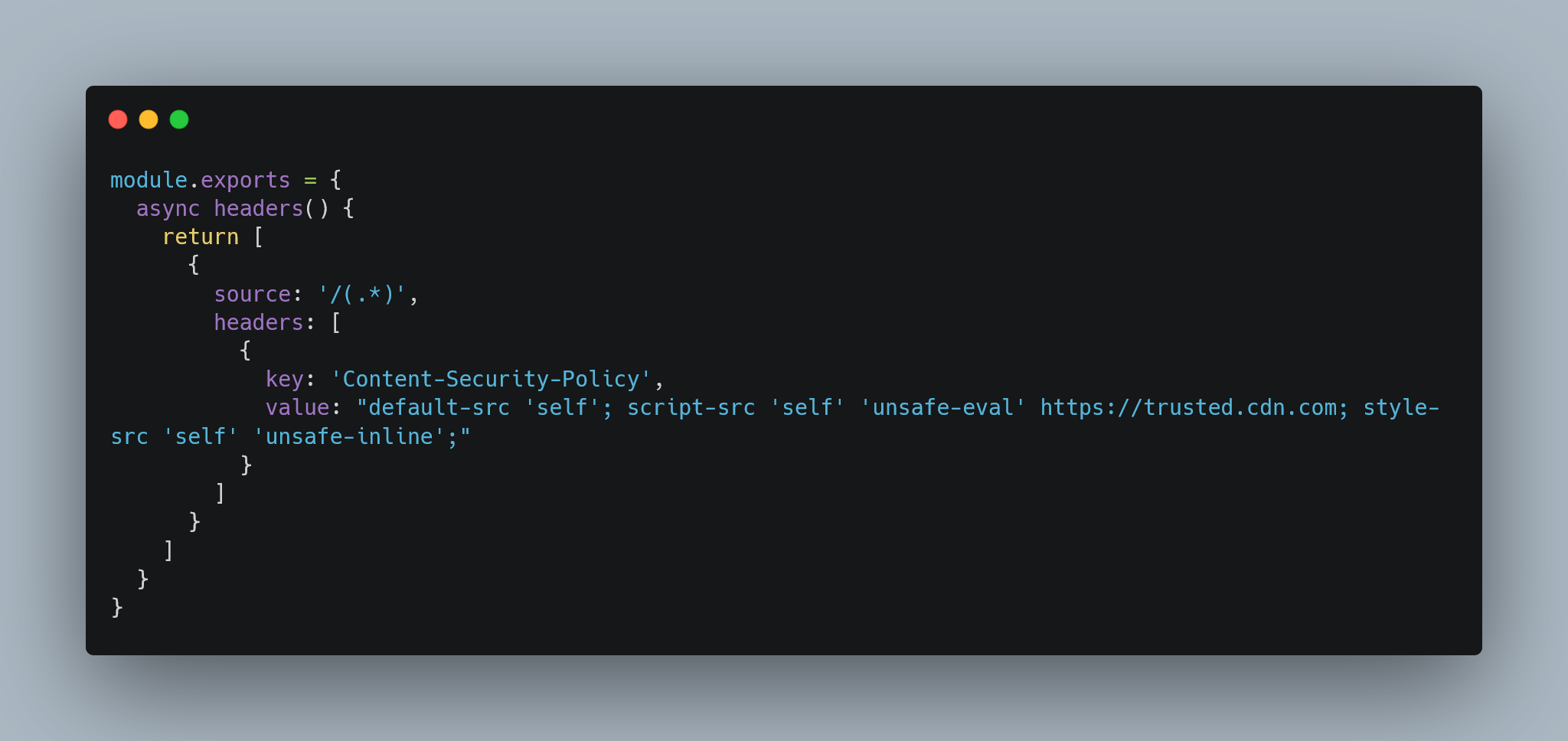
🔒 Content Security Policy (CSP)
- Prevent XSS by restricting resource sources.
- Implementation: Add
Content-Security-Policyheaders vianext.config.js:
🔒 Web Application Firewall (WAF)
- Block malicious traffic before it hits your app.
- Tools: Cloudflare WAF, AWS WAF, or Fastly.
🔒 Automated Security Testing
- Integrate tools into your CI/CD pipeline:
- SAST: SonarQube, ESLint with security plugins.
- DAST: OWASP ZAP, Burp Suite.
🔒 Secure Deployment
- Use containerization (Docker) with minimal base images.
- Enforce HTTPS (Let’s Encrypt + Next.js automatic redirects).
- Monitor logs with services like Datadog or Sentry.
Why Startups Trust Cyber AR for Next.js Security
You’re focused on building your product. Let Cyber AR handle the threats. We offer:
- Next.js Security Audits: Deep-dive assessments of your code, dependencies, and infrastructure.
- Penetration Testing: Ethical hackers simulate real-world attacks to find weaknesses.
- 24/7 Monitoring: Real-time threat detection and incident response.
- Startup-Friendly Plans: Scalable security that grows with you – no enterprise bloat.
Your Next Step: Secure Your Future
Don’t wait for a breach to prioritize security. Protect your Next.js startup today and build a foundation of trust with your users.
Ready to bulletproof your application?
👉 Schedule a Free Next.js Security Consultation with Cyber AR
(Limited spots for startups this month!)
Key Takeaways
- Next.js is powerful but requires proactive security measures.
- Start with fundamentals: Input sanitization, API security, and secret management.
- Automate everything: Dependency scans, testing, and monitoring.
- Partner with experts: Cyber AR provides tailored cybersecurity for startups.
Secure your code. Secure your customers. Secure your success.
Cyber AR – Protecting Innovation, One Startup at a Time.
Related Services
Protect your business with our comprehensive cybersecurity services
Penetration Testing
Comprehensive security testing to identify vulnerabilities before attackers do.
Dark Web Monitoring
Monitor the dark web for compromised credentials and data breaches.
Security Assessment
Evaluate your security posture with our expert assessment services.
Related Articles

Penetration Testing Services Explained
Cyber attackers are relentless. They're constantly on the hunt for weaknesses, particularly in enterprise software that stores critical data. Take HPE StoreOnce, for example, a widely used backup solu...

Enhance Security Monitoring with SOC as a Service
In a world where cyber threats are escalating, businesses need robust solutions to protect their digital assets. SOC as a Service offers a cost-effective and comprehensive approach to security monitor...

Understanding and Defending Against Social Engineering Attacks
In a world dominated by advanced cybersecurity measures, the human element remains the most vulnerable target for social engineering attacks. Learn how to defend yourself and your organization....
Need Expert Cybersecurity Services?
Protect your business with Cyber AR's comprehensive security solutions
Get in Touch