
How Quantity Manipulation Revealed a $7M Online Pricing Flaw?
Description
During a penetration testing engagement at CyberAR, I discovered a critical vulnerability that allows attackers to purchase products at significantly reduced prices through quantity manipulation.
Exploit Begins
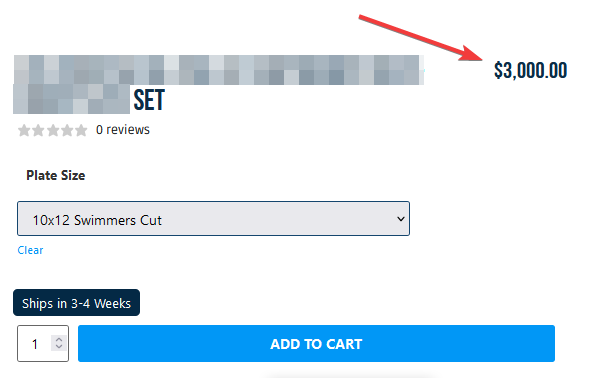
While exploring the website, I identified it as an online store selling various products. After completing some initial test cases, I navigated to the product section to conduct further testing. I selected a product and intercepted the request when I clicked “Add to Cart” to examine the associated request
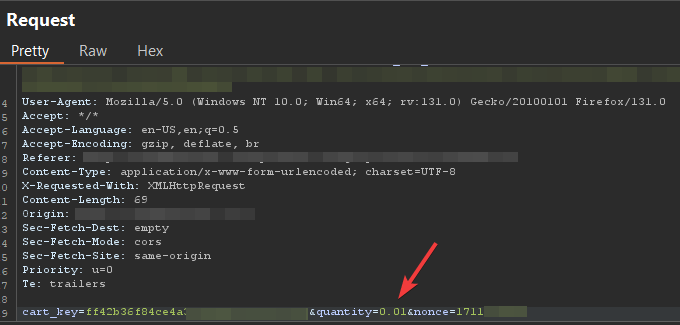
I noticed a parameter labeled “quantity” which determines the number of items to purchase. I attempted to manipulate this parameter by changing its value from 1 to 0.5 Although the response didn’t indicate any changes, I added the product to my cart and then opened my cart to proceed. I decided to test the item update function.
Next, I intercepted the request and increased the quantity to 2. Upon reviewing the request, I noticed the quantity parameter along with some different parameters compared to the previous request. I then changed the quantity from 2 to 0.5 and observed a price reduction from $3000 to $1500.
To realize a greater effect of this vulnerability, I repeated the process, adjusting the quantity to an even smaller value of 0.01
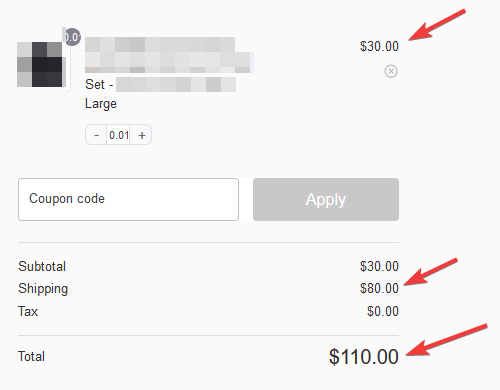
When I clicked on checkout, I noticed the price changed to $30, with an additional $80 for shipping, bringing the total to $110 instead of the original $3080.
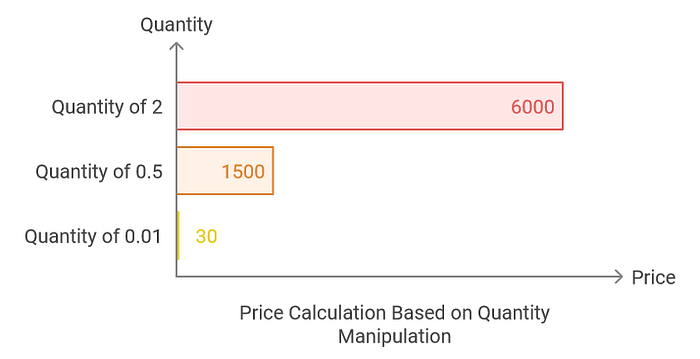
To clarify further, the product price is $3000. When I increase the quantity, the price adjusts accordingly:
- For a quantity of 2: $3000 * 2 = $6000
- For a quantity of 0.5: $3000 * 0.5 = $1500
- For a quantity of 0.01: $3000 * 0.01 = $30
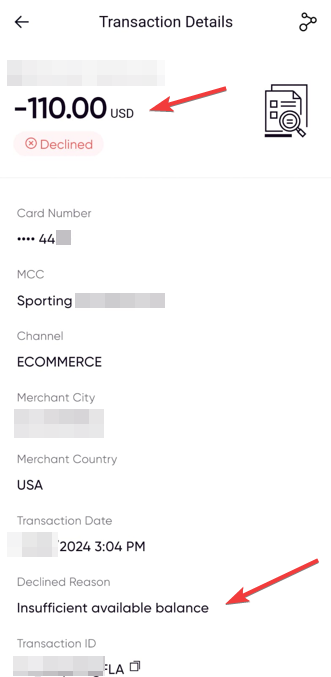
However, I needed to confirm whether this was just a user interface (UI) issue, so I continued with the purchasing process. I entered payment information that did not contain sufficient funds to cover the full amount. Upon clicking “Place Order,” I received a notification indicating that the transaction was successful at $110, rather than the expected $3080. The order was ultimately declined due to insufficient funds on the card.
Test Case for Financial Loss Calculation
Objective: To determine the financial loss incurred by the company due to the exploitation of the vulnerability.
Assumption:
- Number of users: 100
Details:
- Total original price of products: $74,718
- Price after exploiting the vulnerability: $747.18
Calculations:
- Calculate the total original price for 100 users:
- 74,718 × 100 = $7,471,800
2. Calculate the total price for 100 users after using the vulnerability:
- 747.18 × 100 = $74,718
3. Calculate the total financial loss:
- 7,471,800 − 74,718 = $7,397,082
Total Financial Loss:
The total financial loss incurred by the company is $7,397,082
Summary
This discovery highlights a significant security vulnerability related to quantity manipulation in the purchasing process. Attackers could exploit this flaw to acquire products at greatly reduced prices, which poses a serious risk to the integrity of the online store and its revenue. Immediate action is necessary to address and remediate this vulnerability.
Related Services
Protect your business with our comprehensive cybersecurity services
Penetration Testing
Comprehensive security testing to identify vulnerabilities before attackers do.
Dark Web Monitoring
Monitor the dark web for compromised credentials and data breaches.
Security Assessment
Evaluate your security posture with our expert assessment services.
Related Articles

Penetration Testing Services Explained
Cyber attackers are relentless. They're constantly on the hunt for weaknesses, particularly in enterprise software that stores critical data. Take HPE StoreOnce, for example, a widely used backup solu...

Understanding the Three Types of Penetration Test
In the rapidly evolving landscape of cybersecurity, understanding the different types of penetration tests is crucial for safeguarding your digital assets....

Why Manual Penetration Testing Beats Automated Scanners
In today’s digital age, where businesses continually grapple with cyber threats, executives must make informed decisions about securing their assets. Many organizations, eager to enhance cybersecurity...
Need Expert Cybersecurity Services?
Protect your business with Cyber AR's comprehensive security solutions
Get in Touch