
Free Next.js RCE Vulnerability Scanner: Detect CVE-2025-55182 Before Attackers Do
Free Next.js RCE Vulnerability Scanner: Detect CVE-2025-55182 Before Attackers Do
A critical Remote Code Execution (RCE) vulnerability has been discovered in Next.js applications using React Server Components (RSC) and Server Actions. Tracked as CVE-2025-55182, this vulnerability allows attackers to execute arbitrary code on vulnerable servers, potentially leading to complete system compromise.
At Cyber AR, we believe security should be accessible to everyone. That's why we've launched a completely free vulnerability scanner to help you detect if your Next.js applications are affected by this critical security flaw.
What is CVE-2025-55182?
CVE-2025-55182 is a critical Remote Code Execution vulnerability affecting Next.js applications that use:
- React Server Components (RSC) - The new paradigm for building React applications with server-side rendering
- Server Actions - Functions that execute on the server, introduced in Next.js 13+
The vulnerability stems from prototype pollution attacks that can be exploited through specially crafted requests to Server Actions. When successfully exploited, attackers can execute arbitrary code on your server, leading to:
- Data breaches - Access to sensitive user data and business information
- Server compromise - Full control over your application server
- Lateral movement - Potential access to other systems in your network
- Ransomware attacks - Encryption of your data and extortion attempts
How Our Free Scanner Works
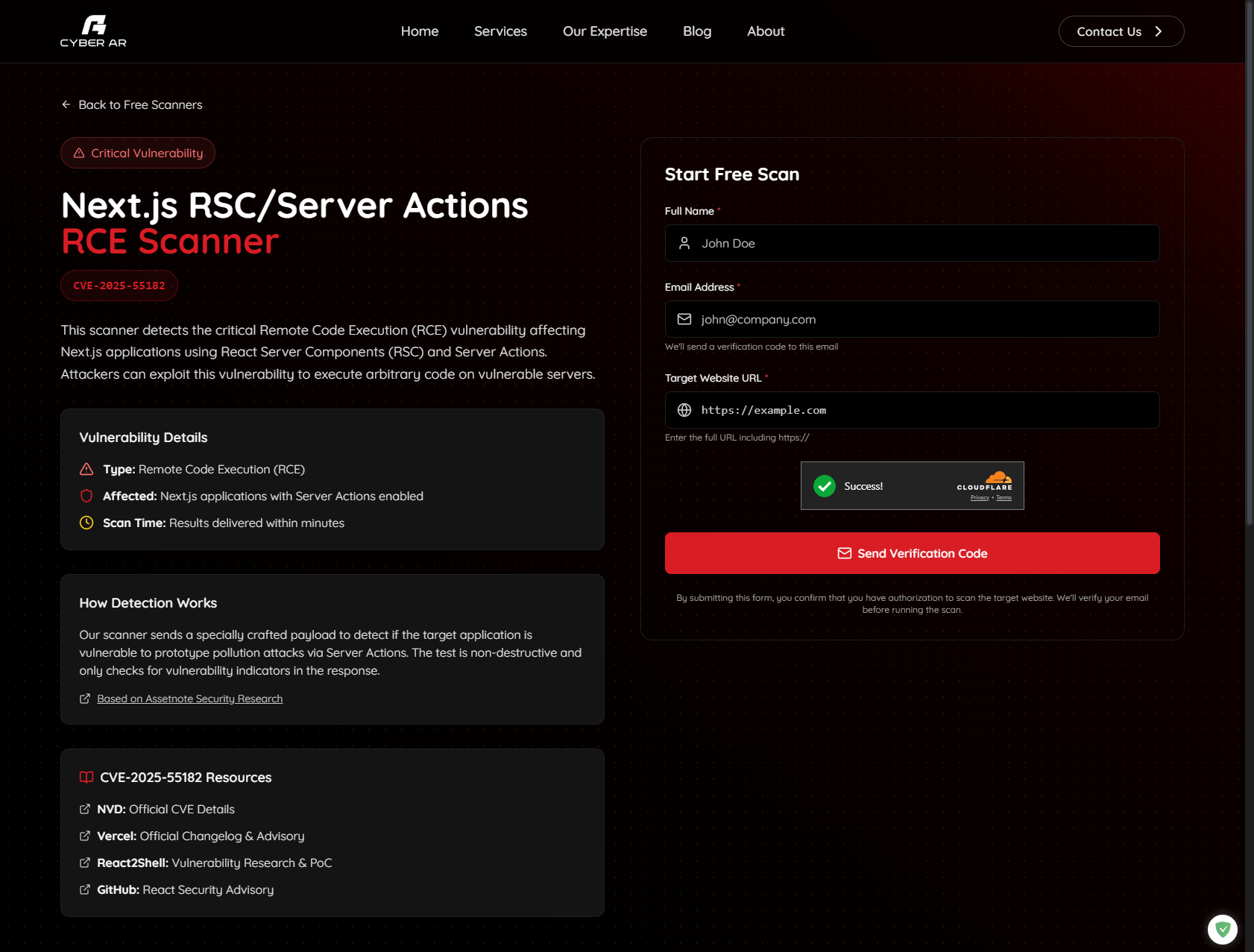
Our scanner is designed to be simple, fast, and non-destructive:
1. Enter Your Details
Provide your name, email address, and the target website URL you want to scan. We require email verification to ensure you have authorization to scan the target.
2. Email Verification
We send a verification code to your email address. This step confirms your identity and ensures that scan requests are legitimate.
3. Receive Results
Once verified, our scanner sends specially crafted payloads to detect vulnerability indicators in the response. The test is non-destructive and only checks for vulnerability signatures without exploiting them.
Results are delivered directly to your email within minutes, including:
- Vulnerability status (Vulnerable / Not Vulnerable / Inconclusive)
- Technical details about the detection
- Remediation recommendations
Why We Built This Scanner
The React2Shell vulnerability research by Assetnote revealed the severity of this issue, and Vercel quickly released patches. However, many applications remain unpatched, leaving them exposed to potential attacks.
We built this scanner because:
- Speed matters - Organizations need to quickly assess their exposure
- Accessibility - Not everyone has the resources for expensive security tools
- Awareness - Helping the community understand and address this threat
Our scanner is based on the Assetnote Security Research and adapted to provide a user-friendly experience.
Available Security Scanners
The Next.js RCE Scanner is the first in our series of free security scanners. We're committed to helping organizations identify vulnerabilities before attackers do.
Coming Soon
We're actively developing additional scanners:
- SSL/TLS Configuration Scanner - Analyze weak ciphers, expired certificates, and misconfigurations
- Subdomain Enumeration Scanner - Discover hidden subdomains and attack surfaces
- Security Headers Scanner - Check for missing or misconfigured security headers
How to Protect Your Application
If our scanner detects that your application is vulnerable, here are immediate steps to take:
1. Update Next.js
Upgrade to the latest patched version of Next.js. Vercel has released security patches addressing CVE-2025-55182.
npm update next
# or
yarn upgrade next
# or
pnpm update next
2. Review Server Actions
Audit your Server Actions for proper input validation and sanitization. Ensure you're not passing untrusted data directly to sensitive operations.
3. Implement Web Application Firewall (WAF)
Consider deploying a WAF to filter malicious requests targeting prototype pollution patterns.
4. Monitor for Suspicious Activity
Enable logging and monitoring to detect potential exploitation attempts.
CVE-2025-55182 Resources
For more information about this vulnerability, refer to these official resources:
- NVD: Official CVE Details
- Vercel: Official Changelog & Advisory
- React2Shell: Vulnerability Research & PoC
- GitHub: React Security Advisory
Start Your Free Scan Today
Don't wait until it's too late. Scan your Next.js applications now and ensure they're protected against CVE-2025-55182.
Key Benefits:
- 100% Free - No credit card required, no hidden fees
- Instant Results - Get your vulnerability report within minutes
- Privacy First - We only scan what you authorize, your data is never shared
- Non-Destructive - Safe testing that won't affect your application
Conclusion
The discovery of CVE-2025-55182 serves as a reminder that even modern frameworks can have critical vulnerabilities. Proactive security testing is essential to protect your applications and users.
At Cyber AR, we're committed to making security accessible. Our free Next.js RCE Scanner is just the beginning. Stay tuned for more free security tools and resources.
Ready to scan your application? Start your free scan now and protect your Next.js applications before attackers strike.
Need comprehensive security testing? Contact Cyber AR for professional penetration testing and vulnerability assessment services.
Related Services
Protect your business with our comprehensive cybersecurity services
Penetration Testing
Comprehensive security testing to identify vulnerabilities before attackers do.
Dark Web Monitoring
Monitor the dark web for compromised credentials and data breaches.
Security Assessment
Evaluate your security posture with our expert assessment services.
Related Articles
CVE-2025-55184 and CVE-2025-55183: Critical Next.js Security Vulnerabilities You Must Fix Now
Critical Next.js vulnerabilities CVE-2025-55184 (DoS) and CVE-2025-55183 (source code exposure) require immediate patching. Learn how to secure your applications.

Critical Security Alert: CVE-2025-66478 (React2Shell) Affects Next.js Applications
Critical remote code execution vulnerability discovered in Next.js App Router applications. CVSS 10.0 severity. Immediate action required for all Next.js 15.x and 16.x users.

Behind the Scenes of a Penetration Test: How We Uncover Hidden Vulnerabilities
Join us as we walk through the real-world process of a professional penetration testing engagement — from reconnaissance to remediation, uncovering hidden risks before attackers strike.
Need Expert Cybersecurity Services?
Protect your business with Cyber AR's comprehensive security solutions
Get in Touch