Critical OTP Verification Flaw in Web App Leads to Account Takeover
In today’s digital age, secure user authentication is paramount to protect sensitive information and maintain user trust. However, during a recent web application penetration test, I uncovered a critical security flaw in the OTP (One-Time Password) verification process of a popular web application. This vulnerability allows attackers to bypass OTP verification, potentially leading to unauthorized access and complete takeover of any user account. This write-up details the steps taken to identify and exploit this flaw, highlighting the urgency for immediate remediation to safeguard user data and application integrity.
Description:
A severe vulnerability in the OTP verification mechanism allows an attacker to brute force the OTP and retrieve a valid OneTimeToken. By exploiting this flaw, an attacker can obtain the victim’s authorization code and gain full access to the victim’s account.
Explanation:
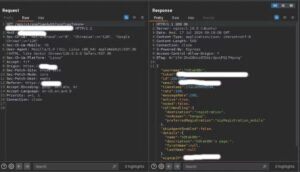
The OTP verification process on the application’s login page is designed to enhance security by requiring users to enter a one-time password sent to their email. However, the application does not implement adequate rate-limiting or protection mechanisms to prevent brute-force attacks. This oversight enables attackers to automate OTP guessing until a valid OTP is identified.
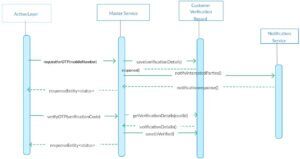
Once a valid OTP is found, the attacker can use the corresponding OneTimeToken to access the victim’s account. This token is then used in subsequent API requests to interact with the account as if they were the legitimate user.
Steps to Reproduce:
- Go to the login page: Navigate to the login page at https://target.io/?login=true.
- Enter the victim’s email address: Input the victim’s email address (e.g., [email protected]).
- Request OTP: The application will send an OTP to the provided email address.
- Enter an invalid OTP and capture the request: Enter an incorrect OTP and intercept the request using a tool like Burp Suite.
- Pass the request to the intruder and assign the code part: Configure the captured request in Burp Suite’s Intruder tool, setting the position for the OTP value to be brute-forced.
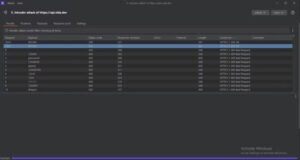
- Start the attack: Launch the attack to brute-force the OTP. The valid OTP will respond with an HTTP status code 200.
- Extract the OneTimeToken: From the valid OTP response, extract the OneTimeToken provided by the server.
- Use the OneTimeToken to access the victim’s account: Use the extracted token in the following request to obtain the victim’s authorization code and all necessary information for account access:
GET /api/v1/oneTimeAuth?oneTimeToken={Victim's-Token} HTTP/1.1 Host: api.target.dev
Conclusion
This critical flaw in the OTP verification process allows attackers to brute-force the OTP and gain unauthorized access to user accounts. To mitigate this risk, the application must implement robust rate-limiting, account lockout mechanisms, and enhanced monitoring to detect and prevent brute-force attacks. Strengthening the OTP validation process is essential to protect user accounts from unauthorized access and potential data breaches.
Related Services
Protect your business with our comprehensive cybersecurity services
Penetration Testing
Comprehensive security testing to identify vulnerabilities before attackers do.
Dark Web Monitoring
Monitor the dark web for compromised credentials and data breaches.
Security Assessment
Evaluate your security posture with our expert assessment services.
Related Articles

Penetration Testing Services Explained
Cyber attackers are relentless. They're constantly on the hunt for weaknesses, particularly in enterprise software that stores critical data. Take HPE StoreOnce, for example, a widely used backup solu...

Why Manual Penetration Testing Beats Automated Scanners
In today’s digital age, where businesses continually grapple with cyber threats, executives must make informed decisions about securing their assets. Many organizations, eager to enhance cybersecurity...

A Guide to Pen Testing for PHP, ASP.NET, and Node Applications
In today's digital age, web applications form the backbone of many businesses, providing critical services and user interactions. As such, the security of these applications is paramount. Frameworks l...
Need Expert Cybersecurity Services?
Protect your business with Cyber AR's comprehensive security solutions
Get in Touch