
Black-box Penetration Testing for Blazor WebAssembly/Server Apps
How to pentest Blazor Server apps?
Introduction – To Blazor Pentest and How you can test the blazor server?
As organizations continue to adopt modern web technologies, the need for securing web applications becomes more critical than ever. One of the rapidly growing frameworks for building interactive web apps is Microsoft’s Blazor, which allows developers to write rich client-side code using C# instead of JavaScript. Blazor comes in two models: Blazor WebAssembly (client-side) and Blazor Server. Despite the strengths and features Blazor offers, applications built on this framework are not immune to vulnerabilities.
This blog provides a comprehensive overview of conducting a black-box penetration test on a Blazor WebAssembly/Server application, identifying common vulnerabilities, and offering guidance on how to mitigate these security risks.
What is the Blazor Framework?
Blazor is a modern front-end framework built on HTML, CSS, and C#. It allows you to create web applications with reusable components that can be executed on both the client (via WebAssembly) and the server. With Blazor, developers can build fast, responsive, and interactive web experiences with familiar C# coding patterns.
What is a black-box penetration test?
A black-box penetration test involves assessing the security of an application from an external, attacker-like perspective. The tester has no prior knowledge of the internal structure, source code, or system architecture. The goal is to simulate a real-world attack, interacting with the application solely through its user interface and publicly accessible components.
In the context of a Blazor WebAssembly/Server application, a black-box tester evaluates both the client-side (WebAssembly) and server-side elements to identify potential weaknesses that could be exploited by malicious actors.
Reconnaissance
The first step in a black-box penetration test is information gathering, or reconnaissance. For a Blazor Web Assembly application, this involves:
- Identifying accessible endpoints: Discovering all public-facing resources and entry points.
- Analyzing the structure of WebAssembly (Wasm) files: Examining the contents of Wasm files to identify business logic and sensitive information.
- Collecting information about libraries, APIs, and resources: Understanding what third-party components and APIs the application depends on.
Blazor applications often use WebSocket connections for real-time communication, particularly in Blazor Server apps. This can add complexity to penetration testing as the communication is more dynamic than traditional HTTP requests. Additionally, Blazor has built-in mitigations for many common vulnerabilities, which makes the process more challenging but still essential to ensure security, especially for custom logic or configurations.
Tools Needed
1. Burp Suite
- Purpose: Burp Suite is an all-in-one platform for web application security testing. It allows penetration testers to intercept, inspect, and modify traffic between the browser and server, making it invaluable for testing APIs, WebSocket connections, and identifying vulnerabilities such as injection attacks or broken authentication.
- Use Case: Intercept WebSocket traffic, manipulate requests, and test API interactions in a Blazor application.
2. ILSpy
- Purpose: ILSpy is an open-source .NET decompiler that allows testers to inspect the internal structure of .NET assemblies, including WebAssembly files (.wasm). It is useful for reverse-engineering Blazor applications to reveal sensitive logic, hardcoded secrets, and other internal functionality.
- Use Case: Decompile Wasm files to examine client-side logic and look for sensitive information like hardcoded tokens or API keys.
3. ChatGPT
- Purpose: ChatGPT can assist with automating tasks, generating scripts, and providing insight into specific vulnerabilities or test results. It can also help with writing reports, creating proof-of-concept (PoC) code, and offering guidance on remediation steps.
- Use Case: Get detailed explanations for vulnerabilities, generate scripts, and produce clean, well-organized reports.
4. Nuclei
- Purpose: Nuclei is a fast and customizable vulnerability scanner that allows testers to run templates for discovering vulnerabilities across a wide range of protocols. It’s effective for large-scale scanning and identifying issues quickly.
- Use Case: Use Nuclei to scan for known vulnerabilities in Blazor applications using templates, such as checking for exposed files like
blazor.boot.json.
How to Carry Out a Penetration Test on a blazor Application
- Initial Setup with Burp Suite:
- Start by opening Burp Suite and customizing the scope of your test to focus on the Blazor application.
- Enable WebSocket interception to capture and inspect WebSocket requests between the client and server. This is essential for Blazor Server applications that use WebSockets for real-time communication.
- Application Exploration:
- Interact with the application and analyze any interesting requests. At this stage, you might not immediately find sensitive requests, but continue exploring the app’s functionality.
- Use search functionality to understand the structure of Blazor and how it communicates with the server.
- Nuclei Scanning:
- Search for Blazor-related vulnerabilities by running templates from the official Nuclei GitHub repository. For example, you might find a template that identifies the presence of the
blazor.boot.jsonfile.
- Search for Blazor-related vulnerabilities by running templates from the official Nuclei GitHub repository. For example, you might find a template that identifies the presence of the

- Analyze the
blazor.boot.jsonFile:- Upon discovering the publicly accessible
blazor.boot.jsonfile, download it to view the list of the application’s resources, such as WebAssembly files, DLLs, and assemblies. - Find references to important files like
CyberAR.wasm(or other platform-specific files).
- Upon discovering the publicly accessible
- Decompiling with ILSpy:
- Use ILSpy to decompile WebAssembly files such as
CyberAR.wasm. - Navigate through the decompiled code to identify sensitive variables, functions, or secrets. For example, you might find references to a
UserTokenor similar sensitive information.
- Use ILSpy to decompile WebAssembly files such as
- Identifying Hardcoded Secrets:
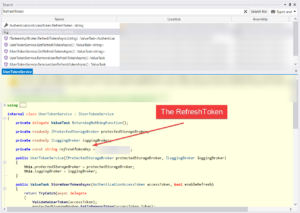
- After decompiling the Wasm file, search for sensitive keywords such as
Token,APIKey, orRefreshToken. In one case, you might find that the JWT refresh token is hardcoded in plain text within the decompiled files.
- After decompiling the Wasm file, search for sensitive keywords such as
- Analyzing and Reporting:
- Once you’ve identified vulnerabilities, use ChatGPT to help analyze the findings and generate a detailed report.
- Your report should include the risks associated with the exposed refresh token or other sensitive information, along with proof-of-concept examples of how these vulnerabilities could be exploited.
Secure Handling of Refresh Tokens in Web Applications
When dealing with refresh tokens, it is crucial to ensure their confidentiality and security throughout the entire lifecycle. According to the guidelines from RFC 6749, refresh tokens may be issued to both web applications and native applications. However, certain key security practices must be followed to ensure that they are not compromised.
Here are the key takeaways from RFC 6749, Section 10.4 regarding the secure handling of refresh tokens:
- Confidentiality of Refresh Tokens:
- In Transit: Refresh tokens must always be transmitted over secure channels. This means using TLS (Transport Layer Security) to protect the token from being intercepted during transmission. TLS ensures that communication between the client and the authorization server is encrypted and authenticated, preventing man-in-the-middle attacks.
- In Storage: Once received, refresh tokens must be securely stored on the client side. They should never be exposed in public-facing code or stored in unsecured locations. The use of secure storage mechanisms, such as HttpOnly cookies or secure local storage (with encryption), is recommended.
- Token Binding:
- The authorization server must maintain a strict binding between the refresh token and the specific client it was issued to. This means that a refresh token should only be valid for the client that received it, and attempts to use it from a different client should be rejected.
- Transmission Security:
- As a best practice, refresh tokens should only be transmitted using TLS with proper server authentication. This ensures that the client is communicating with the correct authorization server and that the token is being sent securely.
Conclusion
Penetration testing Blazor WebAssembly/Server applications presents unique challenges due to the complexity of WebSocket connections and the framework’s built-in security mechanisms. However, with the right approach and tools like Burp Suite, ILSpy, Nuclei, and ChatGPT, testers can uncover vulnerabilities, such as exposed configuration files or hardcoded tokens, and provide actionable remediation steps to ensure the application’s security.
By following this methodology, you can effectively identify and mitigate risks in Blazor applications, ensuring they remain secure in the face of modern cyber threats.
Don’t Forget to check: How to Prepare for Your First Penetration Test: A Guide from Cyber AR
Related Services
Protect your business with our comprehensive cybersecurity services
Penetration Testing
Comprehensive security testing to identify vulnerabilities before attackers do.
Dark Web Monitoring
Monitor the dark web for compromised credentials and data breaches.
Security Assessment
Evaluate your security posture with our expert assessment services.
Related Articles

Penetration Testing Services Explained
Cyber attackers are relentless. They're constantly on the hunt for weaknesses, particularly in enterprise software that stores critical data. Take HPE StoreOnce, for example, a widely used backup solu...

Why Manual Penetration Testing Beats Automated Scanners
In today’s digital age, where businesses continually grapple with cyber threats, executives must make informed decisions about securing their assets. Many organizations, eager to enhance cybersecurity...

A Guide to Pen Testing for PHP, ASP.NET, and Node Applications
In today's digital age, web applications form the backbone of many businesses, providing critical services and user interactions. As such, the security of these applications is paramount. Frameworks l...
Need Expert Cybersecurity Services?
Protect your business with Cyber AR's comprehensive security solutions
Get in Touch